The surge in digital advancements has led organizations to expand their digital presence significantly. While this expansion has brought about numerous advantages for the world, it has also introduced several challenging and darker realities. Data theft, the ease of stealing passwords and infiltrating networks has reached unprecedented levels. Remarkably, a hacker can decipher a password, or a PIN in a mere fraction of a second. What’s even more pressing is the vulnerability inherent in data stored on servers that are not entirely private. A breach anywhere within such a server could potentially jeopardize the security of everyone’s data. This underscores the critical significance of Identity and Access Management (IAM).
Let’s explore the future trends of Cloud IAM that will shape tomorrow’s digital security.
Cloud IAM – Securing the Digital Frontiers
Cloud Identity and Access Management (IAM) is like a vigilant guardian in a bustling metropolis, ensuring that only authorized individuals have access to sensitive information and resources while thwarting potential threats.
IAM stands as a critical component of cloud services, granting control over resource access and management. In a landscape fraught with cyber threats and data breaches, IT managers can fortify data safety by harnessing cloud-based security. Through cloud-based security and identity management (IDM) solutions, organizations gain command over all activities pertaining to identity access and management within the enterprise.
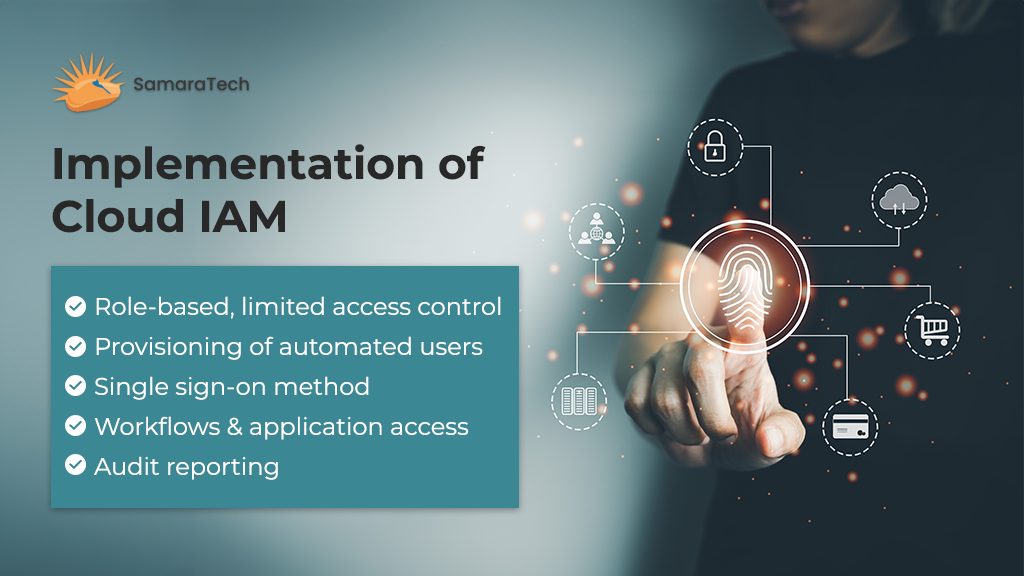
Implementation of Cloud IAM
• Role-based, limited access control
• Provisioning of automated users
• Single sign-on method
• Monitoring of workflows and application access
• Audit reporting
To address security challenges, Cloud IAM solutions emerge as pivotal assets, particularly in fortifying security for the surge in remote workforces generated by the pandemic. These solutions adeptly handle customer interactions on digital channels. Recognizing the paramount importance of IAM, organizations are increasingly contemplating the integration of IAM infrastructure into their cloud architectures.
Cloud Identity and Access management Trends to look out for in 2024?
In a Gartner study, it was revealed that 80% of security and risk management leaders (SRM) view cybersecurity as a business risk rather than a purely technical IT issue. The study further suggests that by the conclusion of 2026, half of C-level executives will give precedence to performance requirements grounded in cybersecurity risk assessments within their employees’ contracts.
Transitioning to cloud IAM empowers cybersecurity leaders with increased flexibility, enabling individuals in various roles across the organization to actively contribute to fortifying the cyber-defense mechanism. This shift allows cybersecurity leaders to decentralize and exert less direct control over numerous imminent cybersecurity decisions, presenting a more effective strategy for organizations.
As we venture into 2024 and beyond, the Cloud IAM is poised to undergo a transformative journey, driven by advancements in artificial intelligence, automation, and decentralized technologies. Here is a sneak peek into the future of Cloud IAM:
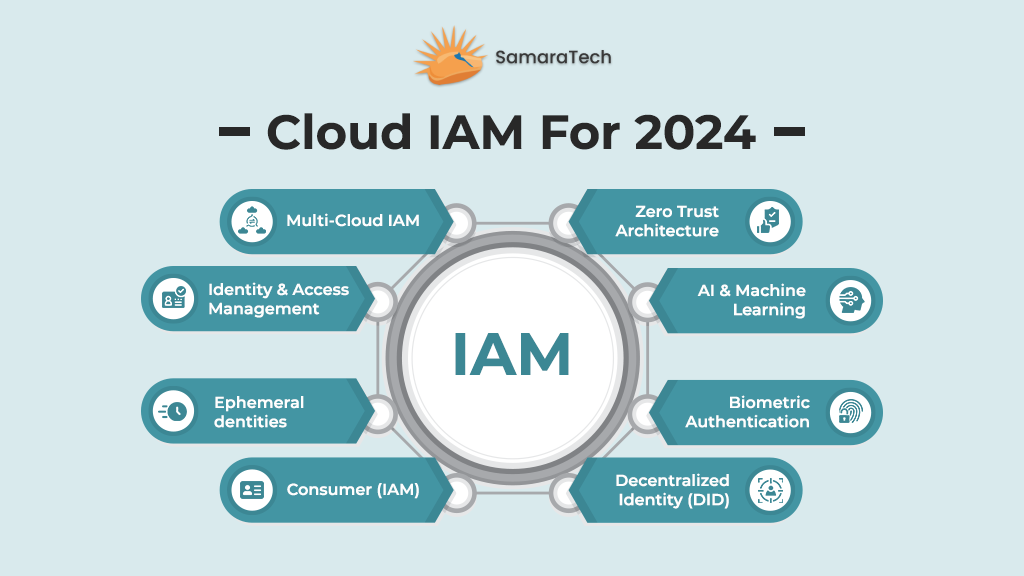
Zero Trust Architecture Becomes the Norm
Zero Trust Architecture is taking center stage, redefining how organizations secure their systems. In 2024, IAM solutions will increasingly adopt a Zero Trust model, where no entity, whether inside or outside the network, is trusted by default. Continuous authentication and authorization will become the new security mantra.
AI and Machine Learning for Advanced Threat Detection
The future of Cloud IAM lies in the hands of artificial intelligence and machine learning. IAM solutions will leverage these technologies to detect and respond to anomalous activities in real-time. Predictive analytics will play a crucial role in identifying potential threats before they escalate, making IAM systems more proactive and efficient in safeguarding sensitive data.
Biometric Authentication Takes Center Stage
Passwords are on their way out. In the futuristic IAM landscape, biometric authentication will dominate. From facial recognition to fingerprint scanning, organizations will increasingly adopt biometric identifiers for enhanced security. This not only provides a more secure authentication method but also enhances the user experience by eliminating the need to remember complex passwords.
Decentralized Identity (DID) for Enhanced Privacy
2024 will witness the rise of decentralized identity solutions. Users will have more control over their personal information, thanks to technologies like blockchain that enable decentralized identity management. This not only enhances user privacy but also reduces the risk of large-scale data breaches.
Consumer Identity and Access Management’s Rise to Prominence
Consumer Identity and Access Management (CIAM) is no longer a niche concern but a pivotal aspect of Identity and Access Management strategy. With an increasing number of businesses relying on digital interactions with consumers, CIAM ensures a secure, seamless, and personalized experience. Expect 2024 to witness a surge in CIAM implementations, as organizations recognize the critical role it plays in customer satisfaction and loyalty.
Ephemeral Identities for Enhanced Privacy
IAM trends are evolving to address the growing concern for user privacy. Ephemeral identities, temporary and revocable access credentials, are gaining traction. This approach minimizes the risk associated with prolonged access and aligns with privacy regulations. In 2024, organizations will explore ways to implement ephemeral identities within their Identity and Access Management strategy to strike a balance between security and user privacy.
Identity and Access Management market Expansion
The IAM market is projected to experience significant growth, driven by the increasing digitization of businesses and the rising importance of robust security measures. As more organizations recognize the need for sophisticated IAM solutions, the Identity and Access Management market will see a surge in innovative offerings, including advanced authentication methods, AI-driven analytics, and integrated CIAM functionalities.
Multi-Cloud IAM Strategies
With the prevalence of multi-cloud environments, Identity and Access Management strategy will evolve to accommodate the complexity of managing identities across various cloud platforms. Organizations will seek unified IAM solutions that provide seamless access management and security across diverse cloud infrastructures, ensuring a consistent user experience and comprehensive security posture.
As we embark on this journey into the future of cloud IAM, organizations must embrace these emerging trends and adapt their IAM strategies accordingly. By leveraging AI, automation, and decentralized technologies, organizations can achieve enhanced security, improved user experience, and reduced operational overhead, paving the way for a secure and thriving cloud environment. By doing so, they not only secure their digital assets but also lay the foundation for a resilient and adaptive cybersecurity infrastructure in the years to come.
Meet your IAM Requirements with SamaraTech
Get the SamaraTech Cloud IAM advantage for your organization. We stand at the forefront of innovation, ensuring that our clients not only meet the challenges of today’s interconnected world but also anticipate and proactively address the security demands of tomorrow. Join us as we redefine what’s possible in the realm of Cloud Identity and Access Management Market. At SamaraTech, data security meets agility, and your digital future is secured with confidence. The journey to the future has just begun, and Cloud IAM is leading the way.




